A simple rate-limiting algorithm that virtually “leaks” tokens at a constant rate, allowing requests to be processed up to a predefined capacity.
Notes
The algorithm works by maintaining a fixed-size buffer, which fills up with incoming packets or tokens at a certain rate.
Note
Leaky bucket is one of the simplest and oldest algorithms used for implementing flow control in networks.
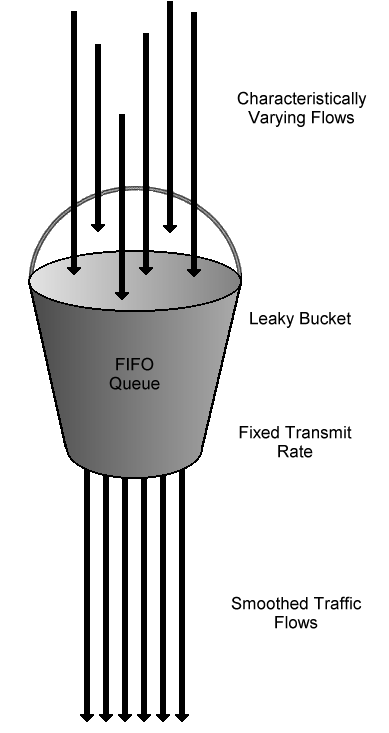
The Leaky Bucket is a Rate Limiting algorithm designed to manage data flow in communication networks. It functions by maintaining a virtual bucket that holds incoming traffic or tokens. The bucket has a constant leakage rate, meaning it virtually “leaks” the contents at a steady pace. This ensures that the buffer doesn’t overflow while allowing for efficient processing of packets within the predefined capacity.
TakeAways
- 📌 The Leaky Bucket algorithm prevents network congestion by regulating incoming traffic through a virtual bucket with a constant leakage rate.
- 💡 It’s simple and easy to implement, making it suitable for various applications.
- 🔍 The algorithm can be customized based on desired throughput and burst size.
Process
- 🔄Bucket Filling: Incoming packets or tokens fill up the virtual bucket at a specified rate, determined by the arrival rate of incoming data.
- ⏳ Leakage Rate: The bucket leaks its contents at a constant pace, ensuring that the buffer’s size remains within predefined limits.
- This leakage rate is controlled by adjusting the interval between packets or tokens as they exit the bucket.
- Capacity Management: By balancing the filling and leakage rates, the Leaky Bucket algorithm effectively regulates data flow in a network while preventing congestion. It can be customized based on desired throughput and burst size.
- 🔁 Dynamic Adjustment: The system continuously monitors incoming traffic and adjusts the filling and leakage rates to maintain optimal performance under varying conditions. This allows the Leaky Bucket algorithm to adapt to different network demands seamlessly.
- 📈 Smoother Data Flow:
- By maintaining a consistent leakage rate, the algorithm ensures that data flows smoothly through the network without overwhelming it, thereby preventing congestion and improving overall system performance.
- Simplicity and Efficiency: The Leaky Bucket’s simple design makes it an attractive choice for implementing rate-limiting in various applications due to its ease of implementation and low computational overhead.
Thoughts
- 📈 Adaptability: The Leaky Bucket can be tailored to meet specific network requirements, such as throughput and burst size.
- 🔁 Simplicity: Its simple design makes it an attractive choice for implementing rate-limiting in various applications.
- 🔄 Continuous Flow Regulation: By maintaining a constant leakage rate, the algorithm ensures that data flows smoothly through the network without overwhelming it.